Censei (pronounced like "Sensei") is a command-line tool I developed that uses the Censys API to identify and analyze suspicious open directories on the internet. The focus is on efficiency, adaptability, and detailed output.
What is Censei?
Censei is a command-line tool written in Go that uses the Censys API to search for suspicious open directories. It automates the process of identifying hosts, checking their availability, crawling directory indexes, and filtering files according to specific criteria.
Why did I develop Censei?
In security research and OSINT work, you constantly encounter the need to systematically search through open directories. Manual searching is time-consuming and inefficient. Censei completely automates this process - from identifying hosts to checking availability and crawling directory indexes.
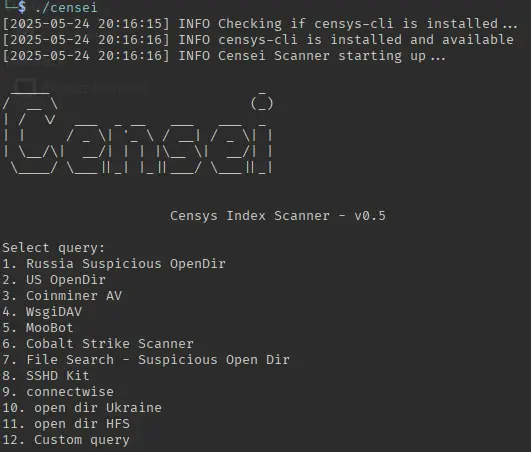
Key Features
- Efficient search for open directories with Censys
- Automatic host availability checking
- Intelligent crawling of directory indexes
- Flexible filtering by file extensions
- Parallel processing for higher speed
- Detailed outputs (raw and filtered)
- Interactive and automated modes
- Special File Checker mode for binary files
- Target-specific file search functionality
Installation and Setup
Prerequisites
Important: Censei requires a valid Censys subscription! The tool does not work without valid API credentials.
- Go 1.20 or higher
- Censys CLI (Installation via pip)
- Censys subscription for API access
Installation
git clone https://github.com/8linkz/censei.git cd censei go build pip install censys
Configuration Files
Create two configuration files:
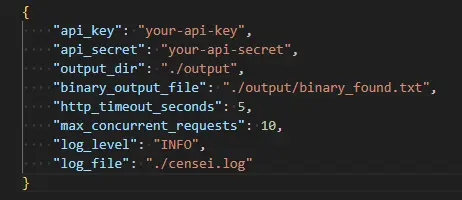
config.json - Basic settings:
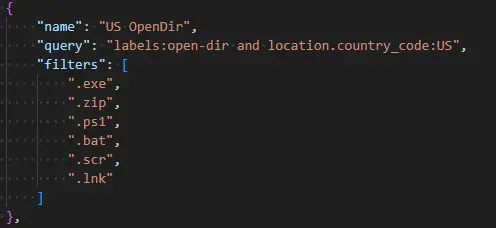
queries.json - Predefined queries:
Practical Usage
Interactive Mode
Simply start ./censei and select from predefined queries:
Direct Queries
For automation or scripts:
./censei --query="labels:suspicious-open-dir and location.country_code:DE" --filter=".pdf,.exe"
File Checker Mode
The File Checker mode is especially useful for targeted searching of specific binary files:
./censei --check --target-file="malware.exe"
This mode skips HTML processing and checks directly for the presence of specific files.
Understanding Output Files
Censei generates three main output files:
- raw.txt - All discovered URLs and files
- filtered.txt - Only files that match filter criteria
- binary_found.txt - Identified binary files
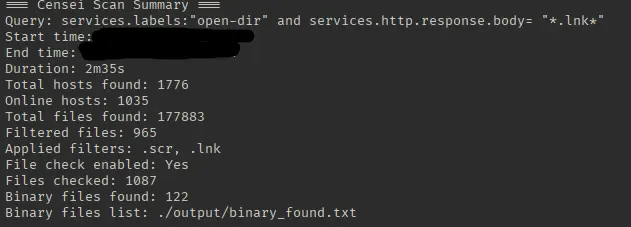
Example Output Format
http://example.com Found file: http://example.com/index.html Found file: http://example.com/data/ Found file: http://example.com/backup.zip With File Checker mode enabled: http://example.com Found binary file: http://example.com/02.08.2022.exe with Content-Type: application/x-msdownload
Use Cases and Security Considerations
Primary Use Cases
- Security research
- Identification of exposed files
- Open-Source Intelligence (OSINT)
- Security audits
- Automated scanning processes
Ethical Usage
Censei is developed for legitimate security research, OSINT work, and security audits. The tool should only be used on your own systems or with explicit authorization.
Final Thoughts
Censei has proven to be an indispensable tool in my daily OSINT work. The combination of automation, flexibility, and detailed output makes it a powerful tool for security researchers.
The tool is open source and available on GitHub. Feedback and contributions are welcome!